The Fraud Pentagon in Action
Overview
The life sciences industry regularly experiences many types of fraud, and it appears instances of fraud arerising. Each year we read about organizations spending billions on fraud and allegations of corruption. So why do we continuously ignore the humans in the loop – especially the gatekeepers? Why is the human element of fraud so taboo to discuss? After all, humans are culpable in the commission of fraud or the payment of bribes, right? Considering the aforementioned and the uptick in Caremark cases,boards and senior management must look at fraud and compliance differently – so I am introducing the Fraud Pentagon™ and the Advanced Meta-model of Fraud™. These advancements are necessary because risk drives the compliance and ethics program, and the success of the program is often dependent on a human’s moral decision-making along with the proper identification and mitigation, if possible, of fraud risks.
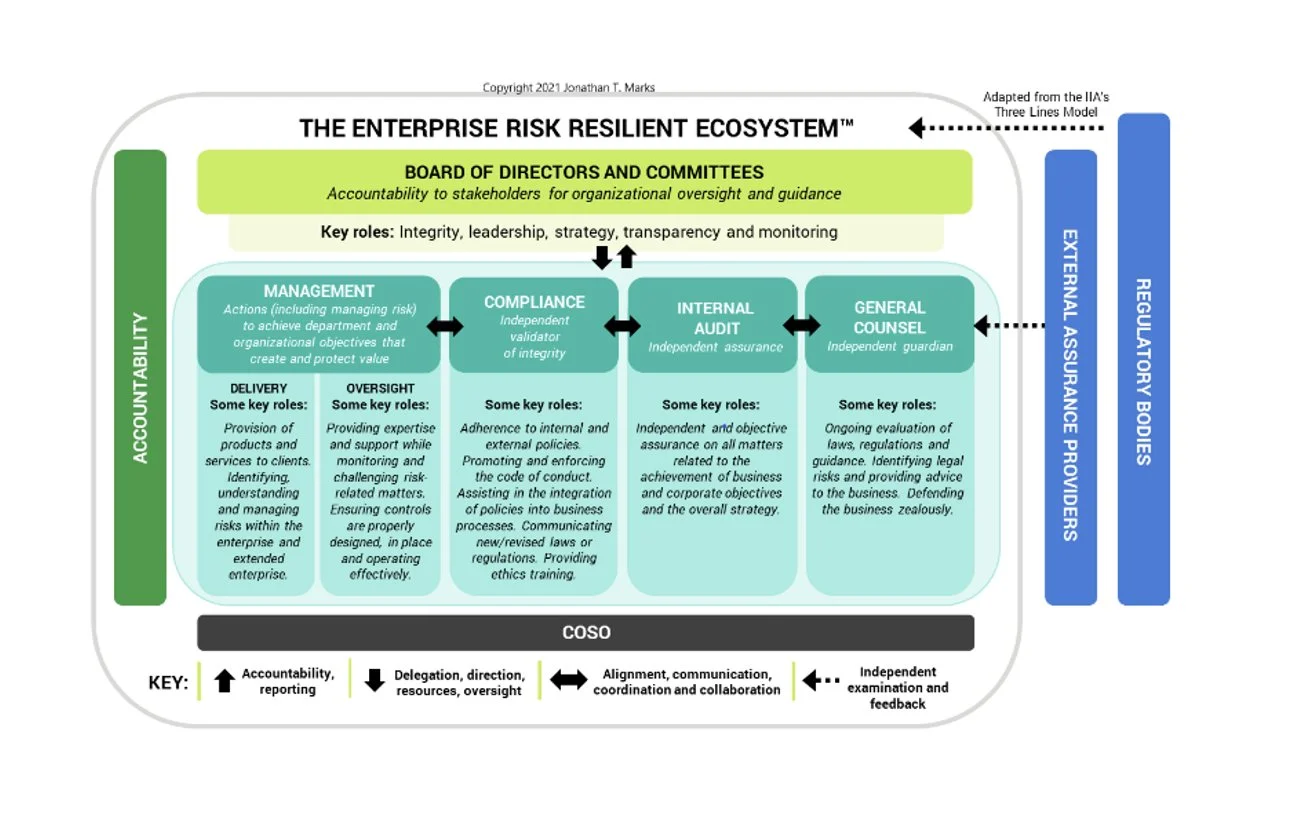
Fraud risk assessments must be accurate and up to date. But it doesn’t end after the assessment. Proper feedback from testing and monitoring is needed to validate and fine tune each risk, which requires aminimum that compliance, internal audit, general counsel, management, and the board work harmoniously to create what I developed and call the Enterprise Risk Resilient Ecosystem.
Today, fraudsters are positioned to have more information and greater access to the organization’s assets. Additionally, the remote work environment, if present, along with strained resources, greatly increases these risks. So, it should be no surprise that data, intellectual property theft, and third-party risk are some of the key risks being monitored by many life sciences concerns.
For example, many organizations have shifted toward cost-saving structures, like outsourcing and global partnerships, because heavy reliance on technology allows these structures to remain highly connected. However, shifting organizational structures also creates an environment for more autonomous fraudsters because individuals are less constrained by time and place due to the increased use of technology. Not only do fraudsters have increased knowledge and access, but organizations have also changed from a ladder structure, common in the 1950s, to matrix organizations where individuals can make changes that impact many. Further, changing pay or incentive compensation structures contribute to the changing fraudster because moving from a more traditional step-up pay structure to a less predictable compensation structure increases the incentive for employees to hit performance targets, even by unethical means.
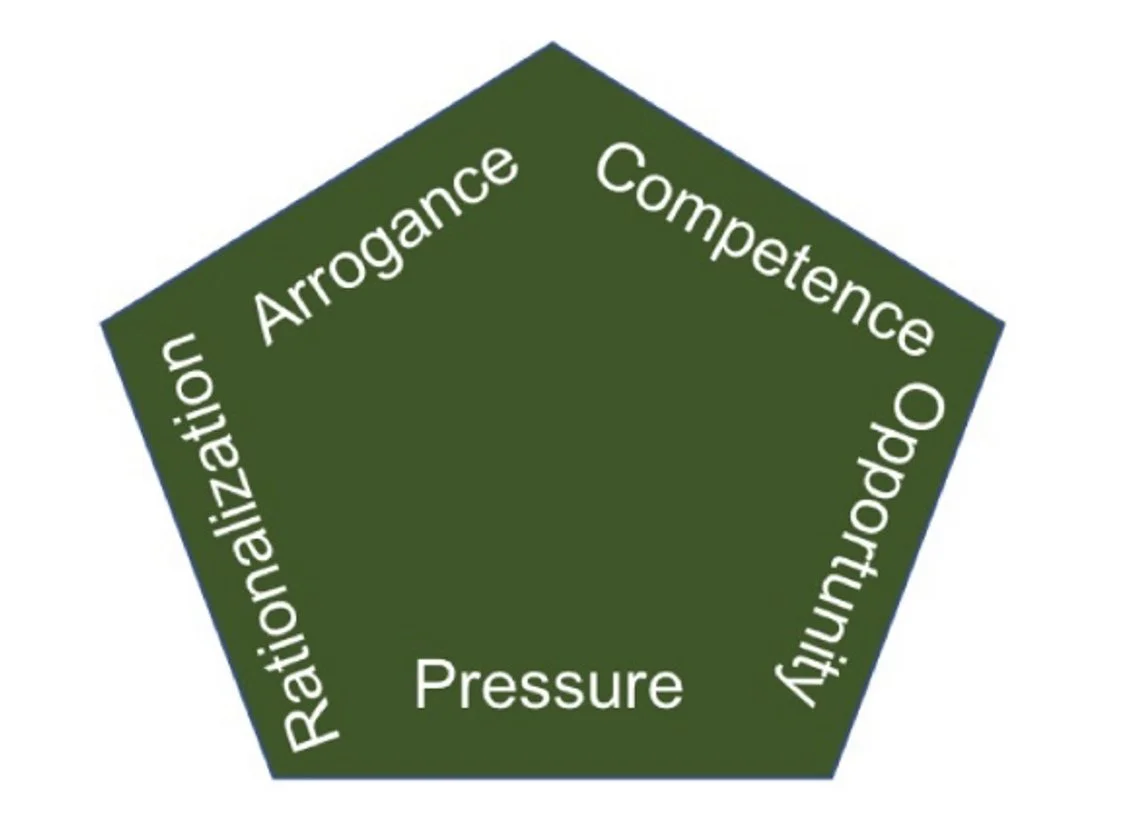
Moreover, corporate culture today focuses on an individual’s status, as demonstrated by wealth and fame, which drives employees to seek larger payouts and more recognition. Remember, incentives are one of the major enemies of a strong control environment and must be diligently monitored to be effective while reducing the corresponding risk. These changes supported my desire to expand the old theory of fraud from a triangle to a five-sided pentagon, developed by Jonathan T. Marks, which considers an employee’s competence or power to perform and an employee’s arrogance or lack of conscience as factors in fraud situations.
Fraud Pentagon was Developed and created by: Jonathan T. Marks
Competence relates to the fraud triangle element of opportunity by expanding the element to account for an individual’s ability to override or circumvent internal controls. Further, the competence element can apply to social control or social capital an individual possesses and can deploy to sell their fraudulent behavior to others, coerce them, or bully them into misbehaving or overlooking the improper conduct.
Additionally, the element of competence can also include perceived competence which applies when an individual would attempt to conceal a situation to avoid being viewed as incompetent or poorly qualified if something should go wrong. Worse, this individual may be completely unwilling to admit incompetence for fear of exposing their lack of knowledge and abilities.
Individuals in this situation may surround themselves with others they view as being easily manipulated or controlled, and this may involve using tactics like overcompensation or threats of job loss to keep these individuals.
People in Line
Adding the element of arrogance or lack of conscience means recognizing the individual’s attitude may be one of a perceived station of superiority and entitlement or greed. This attitude can engender the feeling that corporate policies and procedures simply do not apply to them.
An individual may be provoked to commit fraud when the five elements — pressure, opportunity, rationalization, competence, and arrogance — are unchecked. If individuals who feel entitled and confident in their abilities to commit fraud have sweeping access to corporate information, the risk of fraud increases. Moreover, the situation is markedly worse when these individuals are surrounded by a loose cultural environment, weak tone and conductfrom the top, and poorly designed or non-existent internal controls. This effectively creates the perfect storm for a fraudster, and organizations exhibiting these elements are primed to make headlines and suffer reputational, and potentially financial, loss. Nearly all life science organizations have these five fraud triggers present in some form, but these triggers are exacerbated in organizational environments defined by high pressure.
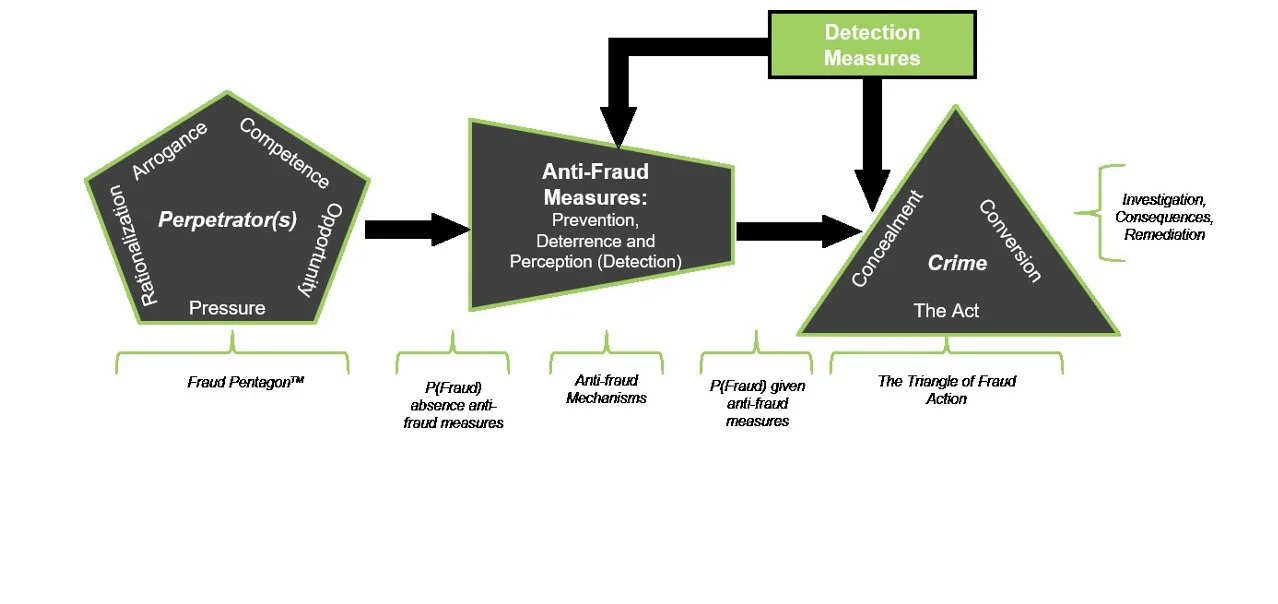
The following model considers the Fraud Pentagon™from the perspective of the fraudster. Placing the fraudster or perpetrator directly inside the Fraud Pentagon helps demonstrate the requisite criteria for a fraudster and considers whether a fraudulent act can be successfully executed and concealed.
The right side of the model demonstrates the elements of the Triangle of Fraud Action. The Triangle of Fraud Action is concerned with the actionable elements of the fraud itself, including the act, the concealment, and the conversion of benefits that accrue to the perpetrator.
Additionally, the model highlights the crucial role of anti-fraud efforts by demonstrating that anti-fraud interventions are squarely between the perpetrator and the crime. This points out that interventions such as internal controls, corporate governance, laws, and regulations can help reduce the incidences and impact of fraud. These interventions can be viewed as prevention, deterrence, and the perception of detection. Generally, anti-fraud efforts are beyond the control of a fraudster. However, the controls still tend to influence the perpetrator’s view of the probability of successfully committing fraud, as far as the fraudulent act, concealment, and conversion.
When developing proactive anti-fraud control policies, consider the following principles:
• Have an effective and empowered audit and compliance committee.
• Establish and enforce a system of effective controls, both internal and external.
• Create and implement a continuous monitoring program over the key business process controls.
• Provide a clear process for reporting suspicious behavior.
• Document ethics initiatives at all levels.
• Develop a response plan in case deterrence fails.
Summary
The elements of fraud that comprised the Fraud Pentagon™ and followed the path of fraud from perpetrator to crime in the Advanced Meta-model of Fraud are a great reminder of how important it is to understand and monitor the human in the loop, including the gatekeepers, the compliance and ethics program, and the design and effectiveness of internal controls. Changing the way we think will increase the overall success of our compliance program and decrease, but never eliminate fraud.